Infamous 'Regin' malware linked to Snowden's NSA files

Researchers say that a powerful computer program that was discovered last year and is linked to campaigns of espionage waged against global targets is strikingly similar to a piece of malware used by the National Security Agency and its Five Eyes allies.
Earlier this month, journalists at Der Spiegel published the source code for a computer program called 'QWERTY' – “a piece of software designed to surreptitiously intercept all keyboard keys pressed by the victim and record them for later inspection,” and said that they hoped the disclosure would “foster further research and enable the creation of appropriate defenses.”
The QWERTY program, according to documents provided to Der Spiegel by former NSA contractor Edward Snowden, is included in an arsenal of malware products used by the National Security Agency and its intelligence gathering allies, colloquially called the Five Eyes. That suite of tools, the German paper said, is used by the US, Australia, Canada, New Zealand and the United Kingdom in order to eavesdrop on targets and conduct other sorts of destructive cyber ops.
According to researchers at Kaspersky Labs who have reviewed QWERTY during the last 10 days, the keylogger’s source code can be linked to 'Regin,' another spy tool that raised eyebrows when it was discovered in late 2014 and alleged to have been used against targets in Algeria, Afghanistan, Belgium, Brazil, Fiji, Germany, Iran, India, Indonesia, Kiribati, Malaysia, Pakistan, Russia and Syria, among others.
READ MORE: Sophisticated ‘state-sponsored’ spying tool targeted govts, infrastructure for years
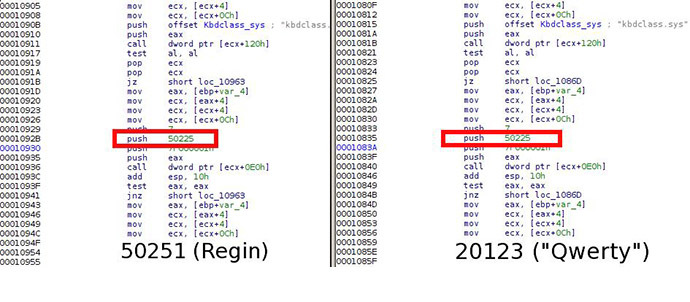
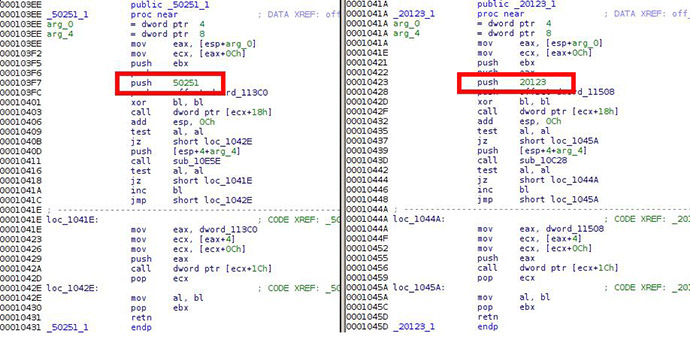
“Considering the extreme complexity of the Regin platform and little chance that it can be duplicated by somebody without having access to its sourcecodes, we conclude the QWERTY malware developers and the Regin developers are the same or working together,” Costin Raiu and Igor Soumenkov, researchers at Kaspersky’s Securelist blog, said on Tuesday.
When details about Regin emerged last November, The Intercept — the online news site founded by Snowden collaborator Glenn Greenwald — said the spyware originated as far back as 2003 and had been deployed against European Union computers and the networks of Belgacom, Belgium’s leading telecommunications company. Researchers with Symantec called it “highly suited for persistent, long term surveillance operations,” and said it had been included in efforts waged against private companies, government entities, and research institutes in Saudi Arabia, Mexico and Ireland.
Less than a month after those initials reports on Regin surfaced, Germany’s Bild newspaper alleged that the spyware had appeared on a USB drive used in the private computer of the head of Germany’s Department for European Policy, but had been contained before spreading further through the nation’s networks.
READ MORE:German govt denies Merkel staffer’s laptop infected by US/UK malware
“Looking at the code closely, we conclude that the 'QWERTY’ malware is identical in functionality” to a plugin used with Regin, Kaspersky concluded this week.
Although the intelligence agencies of the US and its allies are often accused of eavesdropping on adversarial nations — especially in light of the Snowden revelations that have uncovered, among other operations, spy programs that affect innocent Americans — the recent QWERTY analysis suggests that a keylogger specified by the NSA leaker as being an example of a powerful Five Eyes prying tool is likely affiliated with Regin. If correct, the researchers may have furthered the case against the NSA and its intelligence gathering operations, providing more evidence linking the US spy firm to widespread surveillance missions.
Upon Tuesday’s reports from Kaspersky, Spiegel published a follow-up in which the paper re-hashed a report from 2011—two years before the first Snowden leaks—in which a Dutch cybersecurity expert attributed the tool used to hack Belgacom as belonging to either the NSA or its British counterpart, GCHQ.
According to Spiegel, the Regin tool has also been linked to hacks which targeted the International Atomic Energy Agency, based in Austria, as well as the 2011 attack on European Commission computers and other endeavors.












