German govt denies Merkel staffer’s laptop infected by US/UK malware

The German government has denied reports a laptop belonging to a top Merkel aide was infected with the highly-sophisticated Regin virus - malware believed to be a product of British and US spy agencies.
Earlier, Bild reported that Regin spy software was discovered on the USB stick of one of Chancellor Angela Merkel’s senior staff members. Merkel’s Head of the Department of European Policy took the stick home to polish a draft of a speech she had been writing. She saved the document on the USB device using her laptop. At work the next day, virus-scanning software revealed the flash drive was infected with Regin spy software.
READ MORE: Germany to drop investigation into US spying on Merkel – report
Additional checks turned up no infections on any of the 200 high-security laptops in the Chancellery, sources from German security services said, according to the report.
A German government spokesperson refuted the claims on Monday afternoon.
"Such a pattern of attack has explicitly not occurred," Christiane Wirtz said in Berlin. She added that the IT systems of the Federal Chancellery were not infected. "That is, in this context, the most important statement."
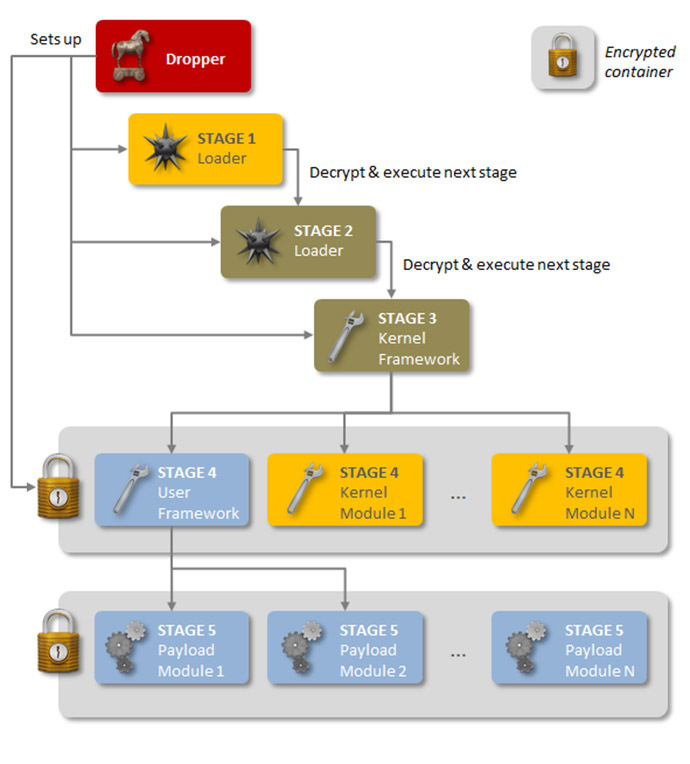
Cyber-security company Symantec first warned of Regin at the end of November. A back door-type Trojan, Regin, is able to“provide its controllers with a powerful framework for mass surveillance.”
READ MORE: Sophisticated ‘state-sponsored’ spying tool targeted govts, infrastructure for years
According to Bild’s report, the virus demonstrates such a“rare degree of technical competence”that indicates it has probably been developed by a nation state – and it could have taken years. Regin is able to fulfill a range of customizable tasks, such as making screenshots, controlling the mouse cursor and stealing passwords, depending on the target of a spying operation.
Media reports associated Regin with the US National Security Agency (NSA) and its British counterpart Government Communications Headquarters (GCHQ). The virus is believed to begin operating in 2008, targeting governments, infrastructure operators, researchers, as well as private individuals and businesses.












