‘Petya’ ransomware may be smokescreen for potentially larger attack
Creating a single file can vaccinate computers against the ‘Petya’ ransomware attack but a ‘kill-switch’ cure for the digital infection has so far eluded cyber security researchers, which may be a sign of worse to come.
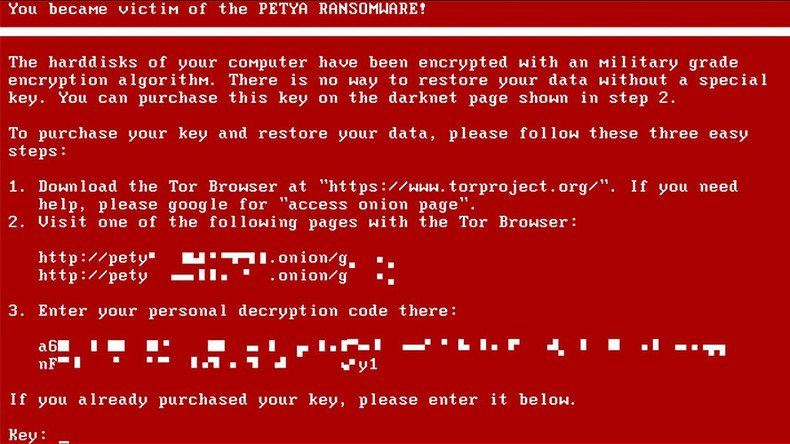
Similar to the WannaCry attacks, users worldwide have been locked out of their systems with screens displaying a demand for a $300 ransom payable in Bitcoin through a specific set of instructions.
“If you see this text, then your files are no longer accessible, because they are encrypted,” the ransom note reads. “Perhaps you are busy looking for a way to recover your files, but don't waste your time. Nobody can recover your files without our decryption service.”
Here's one photo of an alleged infection, provided by a source https://t.co/0EVCTURHmSpic.twitter.com/Zn7sXNIiLm
— Joseph Cox (@josephfcox) June 27, 2017
While the infection has spread worldwide already, the open-source cybersecurity community sprang into action immediately and discovered the digital ‘vaccine.’
Users must simply create a read-only file, with the title ‘perfc,’ and place it in the C:\Windows folder. This will stop the attack dead in its tracks. It does not, however, prevent infection to other machines, it merely protects the individually targeted system, much the same way an immunized human can still be a carrier of infection.
'Time to act': #Snowden calls out NSA over role in #Petya attack https://t.co/fItYYy7ZJnpic.twitter.com/c5hCfn9pG4
— RT (@RT_com) June 27, 2017
“There is low risk of new infections more than one hour after the attack,” the MalwareTech blog stated.
The current ransomware attack is far more limited in scope than its predecessors as it does not attempt to propagate beyond the target network, fuelling speculation that it may just be a cover for another, much larger attack.
Such tactics were allegedly employed during the WannaCry incident which acted as a cover to install the Adylkuzz cryptocurrency miner on thousands of systems worldwide.
#WannaCry XXL? The next ransomware attack will be even worse https://t.co/agSMftskRQpic.twitter.com/qGbfygq4cV
— RT (@RT_com) May 18, 2017
The smaller scale and relative ineffectiveness of the current attack is conspicuous given the recent wave of ransomware hacks worldwide from which the perpetrator could have drawn technical knowledge and inspiration.
The email account to which victims send their ransoms was suspended by the German hosting provider Posteo by noon local time on June 27 and the Bitcoin wallet associated with the attack has not been accessed.
Do not pay the #Petya ransom. You will not get your files back. The email address used is blocked! @SwiftOnSecurity@thegrugqpic.twitter.com/NOzxLz0vul
— haveibeencompromised (@HIBC2017) June 27, 2017
Given the size but disparate nature of the targets – including the Ukrainian central bank, Russia’s state oil company Rosneft, British advertising firm WPP, and US law firm DLA Piper – it appears, initially at least, that the attack was intended to generate chaos and confusion rather than money.
One of the companies which went down was the 3rd largest company in world in revenue. Compared to a Ukraine finance software house.
— Kevin Beaumont (@GossiTheDog) June 28, 2017












