‘NetTraveler’ cyber-spy network compromised over 350 high-profile victims – Kaspersky report

Kaspersky Lab has discovered a years-long cyber-espionage operation that victimized hundreds of high-profile targets in 40 countries. The malware, known as NetTraveler, was used for covert computer surveillance and appears to have originated in China.
The Kaspersky Global Research and Analysis Lab best known for
exposing Flame and Stuxnet - sophisticated spywares launched by
the US government - has uncovered a global cyber-espionage
network targeting the world's diplomatic, government and military
agencies.
In a report published on June 4 the malware that especially
targeted Asian countries was identified as an “advanced
persistent threat” similar to the Red October unveiled in
January.
“Based on the collected intelligence, we estimate the
[controlling] group side to about 50 individuals, most of which
speak Chinese natively and have working knowledge of the English
language,” the report said.
However, nowhere in the Kaspersky report is the Chinese
government accused of any wrongdoing and only speculation links
China to the infection software.
According to the report, NetTraveler was designed to "steal
sensitive data as well as log keystrokes, and retrieve file
system listings and various Office or PDF documents.”
The amount of stolen data discovered on the malware’s
command-and-control servers exceeded 22 gigabytes, with that
being a small fraction of the total data stolen since the rest of
it was previously downloaded by the attackers and deleted from
the servers.
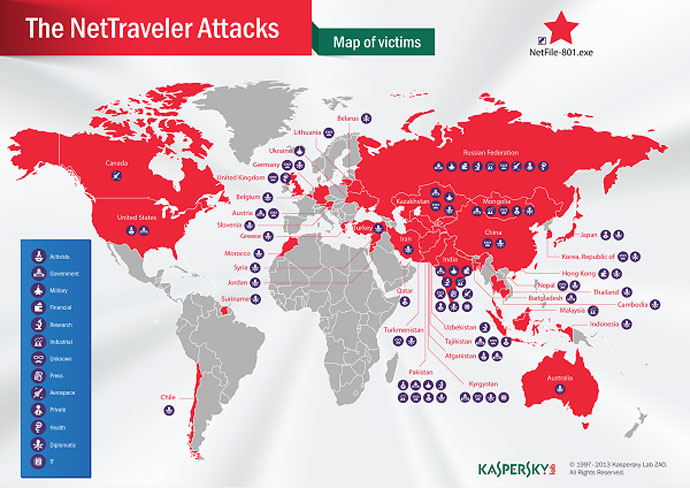
The countries most frequently targeted by NetTraveler – Russia,
India, Mongolia, Kyrgyzstan, and Kazakhstan – all border China.
The first evidence of NetTraveler appeared in 2004, but the
report said the most attacks came between 2010 and 2013.
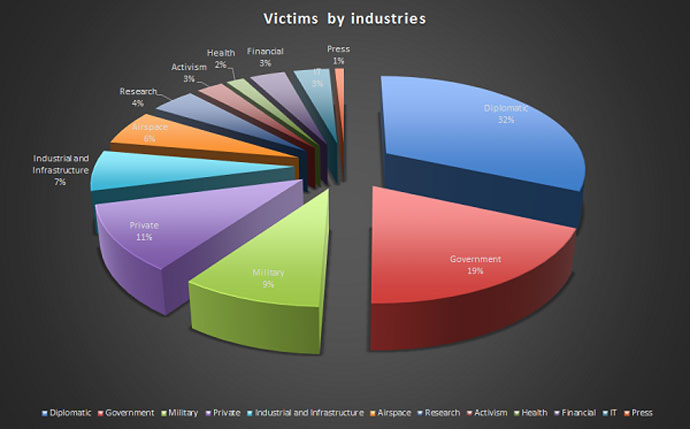
Diplomats were targeted most often, followed by government
workers, and high-level private officials then international
military contractors. Tibetan/Uyghur activists and oil industry
companies also ranked among the favorite targets.
The hackers did not use any advanced vulnerabilities and relied
on phishing attacks, which often distribute infected links via
email or social media.
“NetTraveler victims get infected through spear-phishing
attacks using Office documents which exploit two publicly known
vulnerabilities,” the report states with analysts surprised
that such unsophisticated attacks can still be successful with
high profile targets. “Although these vulnerabilities have
been patched by Microsoft, they remain effective and are among
the most exploited in targeted attacks.”
The researchers discovered that at least six NetTraveler targets
– a Russian military contractor, a government organization in
Tajikistan, and embassies in Belgium, Iran, Kazakhstan, and
Belarus – were previously hacked by the Red October campaign that
was likely launched from Eastern Europe. Kurt Baumgartner, a
senior security researcher for the Americas on the Global
Research and Analysis Team at Kaspersky, told DarkReading.com the
attempts from separate phishing schemes indicates those locations
are highly valued.
“Threat actors infiltrate victims simultaneously and may or
may not be concerned about victim overlap,” he said. “Most
likely, with these two groups in particular, the operators have a
specific set of tasks at the victim organizations. If they happen
to see another piece of malware on the target network, and it
doesn’t interrupt their operation, they just go back to
completing their assignments.”