Tor-provided web anonymity not PRISM-proof – Microsoft security guru

The Tor anonymity network cannot provide internet users shelter from government hackers and cyber criminals, a top Microsoft security expert has revealed.
"There is no such thing as really being anonymous on the internet. If [hackers and government agencies] want you, they will get you," Andy Malone, of Microsoft Enterprise Security and founder of the Cyber Crime Security Forum, said at the Microsoft TechEd North America 2014.
While The Onion Router (Tor) remains more resilient than alternatives such as virtual private networks, cyber criminals are able to exploit weaknesses in the system.
“At the moment the Tor network's security has never been broken, but there are flaws around it that can be exploited,” Malone said.
One such example is the fact that Tor still uses third-party add-ons, allowing snoops to track, monitor and steal data from its users.
"Tor leaks do occur through third-party apps and add-ons, like Flash. If I was doing forensics on you and thought you were on Tor I wouldn't attack the network I'd attack the weak areas around it.
Malone says that both the National Security Agency and its UK counterpart, GCHQ, are monitoring “hundreds of Tor relays” and are constantly trying to find ways to break down the secure network. By its very nature, Tor cannot and does not protect against monitoring of traffic on the edges of the Tor network, where traffic comes in and goes out. While it can protect against the process of intercepting and examining messages – traffic analysis – it cannot prevent traffic confirmation.
A zero-day (or zero-hour or day zero) attack or threat is an attack that exploits a previously unknown vulnerability in a computer application.
"You can get people on Tor in a variety of ways. You could do a time attack, which involves catching traffic between relays. You could also do entry and exit node monitoring, which involves dropping a zero-day on the actual machine accessing Tor or hosting an exit node and monitoring what's going in or out of it."
Honey Pots and the Dark Web
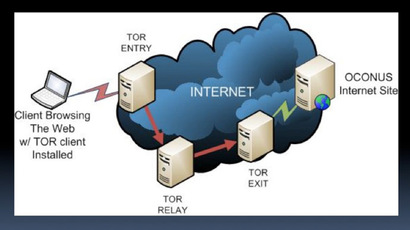
Onion routing was initially designed at the US Naval Research Laboratory to protect the security and privacy of network communications. Tor was originally designed to shield intelligence gathering operations from open sources and protect military communications over public networks. The network works by routing traffic through multiple nodes in an effort to help mask the identities of its users.
It allows for the creation of “invisible websites” with the .onion extension that can’t be accessed using conventional browsers like Google Chrome or Firefox. Such sections of the internet comprise part of the Deep Web – the part of the web not indexed by search engines.
Tor is made possible through a network of donated servers that exchange encrypted data amongst each other before returning through an “exit node,” or the server that is connected back to the internet. The goal is to obscure just where traffic is moving, in order to evade any observers. Exit Nodes are on the edge of the Tor network, meaning traffic from this node can be traced back to its IP address.
While many law-abiding citizens and those seeking to circumvent government censorship have embraced Tor, the notorious online market Silk Road, sometimes called “the ebay for drugs”, was also a hidden Tor service.
Malone said that law enforcement agencies are actively working on
more direct ways to penetrate the Tor network and monitor its
users.
"I work with, and issue recommendations for, law enforcement and I'm telling you now, the dark web is heavily monitored. The NSA and GCHQ are already monitoring hundreds of Tor relays and exit nodes and trying to find ways to break the network down," he said.
He further warned that users should be aware that the NSA and GCHQ are installing hundreds of onion routers in order to capture and analyze traffic. If a user visits the Deep Web, they should be aware of the existence of honey pots, or trap websites that appear to be part of the network, but are in fact created by law enforcement to catch criminals.
That the NSA and GCHQ are targeting Tor is no secret. Last October, documents leaked by NSA whistleblower Edward Snowden revealed that the intelligence agencies are working extensively towards compromising the computers of people who browse the internet with Tor.
According to the Guardian’s James Ball, Bruce Schneier and Glenn Greenwald, the NSA’s “current successes against Tor rely on identifying users and then attacking vulnerable software on their computer.”
“While it seems that the NSA has not compromised the core security of the Tor software or network, the documents detail proof-of-concept attacks, including several relying on the large-scale online surveillance systems maintained by the NSA and GCHQ through internet cable taps,” the writers added.